
Zapraszamy Was na kolejny live stream prowadzony przez Grześka Wypycha: bezpośredni link tutaj, startujemy 22.04.2020, 20:00. Temat: Wykorzystanie symbolicznej analizy do wyszukiwania błędów bezpieczeństwa w binarkach i tworzenia exploitów na bazie autorskiego plugina do Binary Ninja. Opis: Czytelniku, udało ci się przejść kursy exploitacji binarek ? Jeśli tak gratuluje, pewnie nabity…
Czytaj dalej »
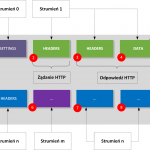
Podatność została niedawno temu załatana w HAProxy i została od razu zaklasyfikowana jako krytyczna. Twórcy HAProxy piszą asekurancko, że nie powinno się dać wykorzystać luki, no może co najwyżej być crash, a w nowoczesnych systemach to już w ogóle jest tyle zabezpieczeń że hej! A tym czasem googlowy projekt zero opublikował…
Czytaj dalej »

Vice donosi o dwóch 0-dayach na Zooma: jeden z nich to „przyjemny i czysty RCE” (Remote Code Execution) w zoomowej aplikacji na Windowsy. Druga podatność dotyczy klienta na MacOS (choć nie jest to RCE). Istnienie tych podatności, dziennikarz Vice potwierdził w trzech niezależnych źródłach, choć sceptycy powiedzą – pokażcie exploita…
Czytaj dalej »

Dzisiejszy vulnz to całkiem świeża podatność CVE-2020-3843. Zobaczmy: Attached is a work-in-progress exploit for CVE-2020-3843, a buffer overflow in AWDL (…) Currently this poc demonstrates the ability to remotely dump device physical memory regions over the air with no user interaction on iPhone 11 Pro running iOS 13.3. Dość ostre, prawda? Słowo wyjaśnienia czym…
Czytaj dalej »

Trzy częściowy techniczny opis podatności można znaleźć tutaj. W skrócie, korzystając z odpowiednio spreparowanej wiadomości iMessage (taki applowy SMS) można było poomijać różne mechanizmy ochronne iPhone-ów, w tym wyskoczyć z sandboksa, finalnie otrzymując pełen dostęp root. Co dalej? Dostęp do SMS-ów, mikrofonu, kodów 2FA, aparatu, danych – w skrócie tak…
Czytaj dalej »

Może ktoś jeszcze pamięta aferę z Hacking Team? TLDR: firma skupowała exploity na podatności 0-day. Ktoś się do nich kilka lat temu włamał i upublicznił zarówno exploity jak i inne dokumenty (okazało się że kupowało tam również polskie CBA…). Obecnie hacking team został przejęty i zaprezentowany pod nieco inną nazwą:…
Czytaj dalej »

Ceny macie zaprezentowane w tym miejscu. Największa pojedyncza wypłata to aż $1 000 000 i dotyczy podatności klasy RCE (remote code execution) dotykającą chip Titan M, używany w googlowym Pixel 3: This year, with Pixel 3, we’re advancing our investment in secure hardware with Titan M, an enterprise-grade security chip custom built…
Czytaj dalej »

… i kilka jeszcze innych produktów zostało przejętych w ramach konkursu tianfucup, odbywającego się na chińskiej ziemi. Całość to odpowiedź na niezbyt przychylne (delikatnie rzecz ujmując) patrzenie chińskich władz na występowanie rodzimych badaczy na zewnętrznych konferencjach tego typu. Uczestnictwo w lokalnej imprezie jest też podgrzewane naprawdę solidnymi nagrodami. Przykładowo, około…
Czytaj dalej »

Podatność zaprezentowano w ramach tegorocznego konkursu Pwn2Own. Błąd jest klasy buffer overflow i występuje w komponencie baseband telefonu (czyli komunikującym się bezprzewodowo z siecią GSM). Wystarczy więc odpowiednia stacja bazowa i wysyłamy złośliwą komunikację do telefonu. Poniżej wprawdzie widać, że badacze utworzyli zdalnie swój plik na telefonie, ale informacja że…
Czytaj dalej »

Podatność o której pisaliśmy parę miesięcy temu dotyka wprawdzie Windowsa 7 (i niższych), ale umożliwia bez żadnej interakcji ofiary na otrzymanie pełnego dostępu administracyjnego na atakowanej maszynie. Sytuację pogarsza fakt, że w Metasploicie od jakiegoś czasu gotowy jest exploit na lukę. Tymczasem ktoś rzeczywiście zaczął atakować systemy dostępne z Internetu…
Czytaj dalej »

Informację o nowej wersji przeglądarki oraz podstawowe informacje o zlokalizowanych poważnych błędach podał Google. Błędy są na tyle istotne, że firma na razie nie podaje szczegółów technicznych, zasłaniając się (słusznie) bezpieczeństwem użytkowników: Access to bug details and links may be kept restricted until a majority of users are updated with a…
Czytaj dalej »

Krótką informację o pojawieniu się tego eksploita opublikowaliśmy niedawno. Obecnie pojawił się ciekawy wywiad z samym autorem, ujawniającym więcej szczegółów działania. Podsumowując: Exploit umożliwia wykonanie dowolnego kodu atakującego na poziomie BootROM-u, zawiera on w zasadzie pierwszy kod który uruchamia się po włączeniu telefonu. Wygląda to niezbyt optymistycznie, bo jak widać kontrolujemy…
Czytaj dalej »

Exploit o kryptonimie checkm8 (czyt. szachmat) został właśnie ogłoszony i udostępniony. Całość dotyka ogromnej liczby modeli urządzeń Apple: Most generations of iPhones and iPads are vulnerable: from iPhone 4S (A5 chip) to iPhone 8 and iPhone X (A11 chip). Exploit jest dostępny tutaj, i może być użyty jako fragment narzędzia realizującego…
Czytaj dalej »
Podatności w Remote Desktop Services Microsoft opisuje tutaj: CVE-2019-1181, CVE-2019-1182, CVE-2019-1222, CVE-2019-1226. Nie owijając zbytnio w bawełnę: W RDP jest podatność klasy RCE, którą można wykorzystać bez uwierzytelnienia przez przesłanie odpowiednio złośliwej komunikacji. Podatność nie wymaga interakcji ofiary, a atakujący może wykonywać dowolne polecenia na docelowym systemie, łącznie z tworzeniem kont z…
Czytaj dalej »
Windows umożliwia wysyłanie komunikatów pomiędzy oknami (np. notepad oraz cmd). Okna jednak mogą działać w kontekście różnych użytkowników (np. notepad – normalny użytkownik, cmd administrator. Nie chcielibyśmy raczej mieć nieskrępowanej możliwości komunikacji z takiego notatnika do cmd (wtedy ten ostatni mógłby być potencjalnie zaatakowany). Za ochronę w tym miejscu odpowiada…
Czytaj dalej »











