Żądny wiedzy? Wbijaj na Mega Sekurak Hacking Party w maju! -30% z kodem: majearly
HP LaserJet Pro printers remote admin password extraction
Introduction
Some of the networked HP LaserJet printers have hidden URLs hardcoded in the firmware. The URLs are not authenticated and can be used to extract admin password in plaintext – among other information like WiFi settings (including WPS PIN).
Models affected
HP LaserJet Pro P1102w, HP LaserJet Pro P1606dn, HP LaserJet Pro CP1025nw, HP LaserJet Pro M1212nf MFP, HP LaserJet Pro M1213nf MFP, HP LaserJet Pro M1214nfh MFP, HP LaserJet Pro M1216nfh MFP, HP LaserJet Pro M1217nfw MFP, HP LaserJet Pro M1218nfs MFP, Possibly others(?)
Details
There are at least two interesting URLs, which can be accessed without authentication:
http://IP_ADDRESS/dev/save_restore.xml
This contains probably most of configuration paramethers of the device.
For example we have http password value here:
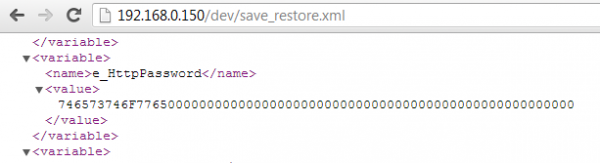
The password seems to be encrypted on the screen above… but wait, the value contains hex representation of the admin password in plaintext (!), ie.: 0x746573746f7765 is: testowe
In other words, using this method, the admin password can be extracted regardless of its complexity.
Other interesting paramethers (there are more than one hundred of them):
- e_cloudPrinterID
- e_cloudPrinterKey
- e_StatusLog
- e_CartNVRam
- e_WifiStaConfig
If a printer is WiFi enabled, than some WiFi info can be obtained:
http://IP_ADDRESS:8080/IoMgmt/Adapters/wifi0/WPS/Pin
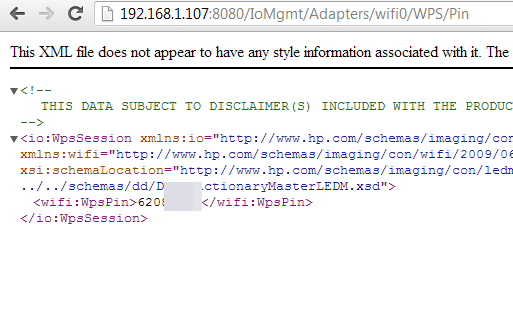
So we have WPS PIN here, and where to look for SSID? Yes, the previous save_restore.xml link (e_WifiStaConfig variable).
History
- 19.04.2013 vendor notified
- 19.04.2013 initial vendor response received
- 24.04.2013 issue confirmed
- 26.07.2013 new firmwares released
- 31.07.2013 issues summary published by vendor
- 02.08.2013 disclosure
— michal.sajdak<at>securitum.pl


